Category: Electronic Access Control Systems
Does Your Access Control System Tell You All About The Day’s Activities?
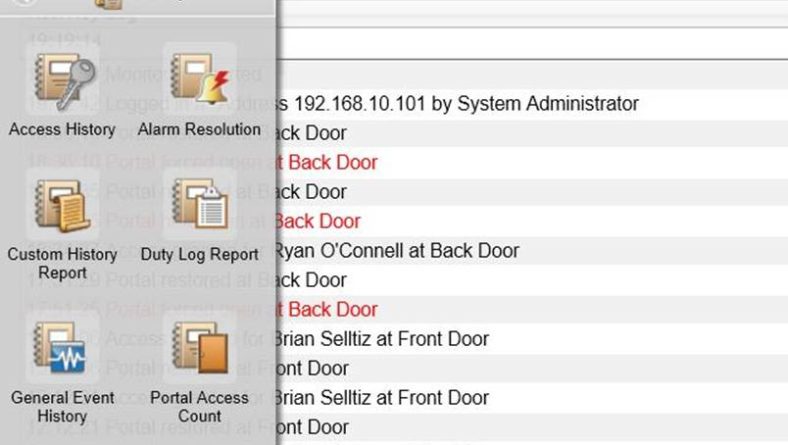
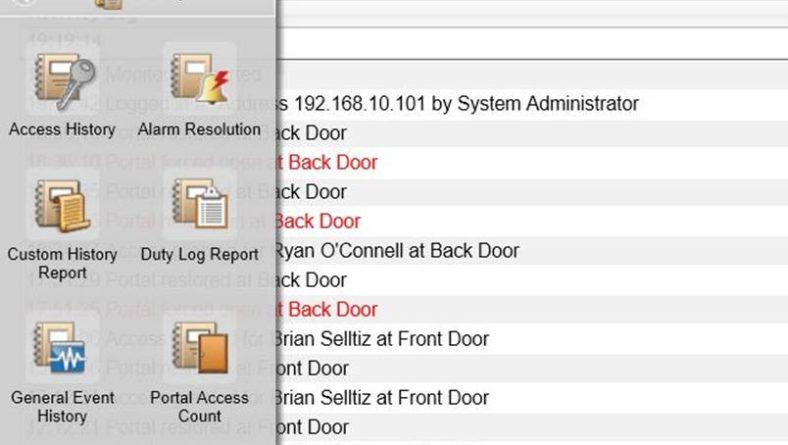
Does your EAC system speak to you? Probably not, but that doesn’t mean it shouldn’t communicate important information to you on a regular basis. Access control reports are a powerful yet often underutilized function of a modern access control system. Systems such as those manufactured by S2 www.s2sys.com offer users a powerful interface which allows managers to get the information they need about their building in real time. Additionally, reports can be automated to arrive in your inbox at a specified time or day.
Some of the more common reports are:
Access History Reporting
Parameters: Person; Event Type; Date Range; Door ID
Best Use Examples:
-Where is ‘Harold’ always disappearing to? Run a report to see when and where ‘Harold’ has been during the last month.
-Think an employee is testing out to see if the door is locked to that secure storage? Run a report to see every time someone tried to get into an area where they did not have the proper access to do so.
-Had an incident at the plant needed more info? Run a report to see everyone who was in the office on the day in question.
-Weekend hijinks? Automate a report to email you every Monday morning to show who was in the building over the weekend.
Compliance Reporting
Parameters: Door ID
Best Use Examples:
-Do you have schedule II drugs or other items that require only certain people access that storage area? Run this report on demand to confirm who has access to critical areas. Even better, automate this function, so it is delivered to your inbox at the beginning of the month like clockwork.
Credential Audit Reporting
Parameters: Time Span; Credential Status
Best Use Examples:
-When an employee is terminated their credential should be disabled, but we all know that sometimes things get missed. Run this report to see who has not used their badge in the last 30 days and then disable it.
-Vendors are notorious for never returning badges (not us of course). Run this report and quickly identify vendors who no longer require access to your building and disable their badges.
Utilization Reporting
Parameters: Date Span; Door ID; Person
Best Use Examples:
-Most often we see this report used to deliver relevant statistics on Turnstile utilization. Turnstiles are now standard security equipment in larger buildings throughout New York City / NYC, use this report to get true numbers of people passing through per week, month, year, etc.
Digital Provisions specializes in installing and upgrading Electronic Access Control Systems to the latest state of the art IP based systems, all with little or no disruption to your business. Contact us for a no obligation site security design which will give you the information you need to secure your facility properly.
Back Up Your Access Control System Before It’s Too Late!


In the wake of any disaster, the race is on to restore things to normal. If your place of business is damaged by flood water, fire, electrical surge, or other means, chances are your electronic equipment could be damaged and in need of replacement. If this happens to you, does your access control system provide built in offsite backup? This feature is included in S2 Security access control systems and it can make redeploying your security measures a task that can take minutes instead of days.
In the S2 Security box’s web interface, you will find a feature called “FTP Backup”. This feature allows the user to create a full backup of the access control database and save it offsite at a secure location automatically. Users can always manually download a copy of the database, which is recommended prior to making any major changes to the system.
Each employee will have their own access control cards, access schedules, and other security related data. Having an FTP backup from S2 Security can save countless hours that would otherwise be spent tracking down and collecting individual employees’ access cards, rebuilding the access control database, reprogramming locks and door components, and resetting schedules manually.
The FTP backup method, on the other hand, is a completely different experience. After diagnosing the point of failure and replacing the damaged equipment, the restoration process can be completed in minutes once the off-site backup file is uploaded to the panel. As with any backup method, it is recommended that the data is periodically checked to ensure that the system is working properly and the system restores properly. Simple, automatic and invaluable if needed, be sure to include your access control system in your contingency planning backup procedures.
Digital Provisions specializes in installing new systems or upgrading legacy Electronic Access Control systems to the latest state of the art IP based systems, all with little or no disruption to your business.
Why Electronic Access Control Systems Are Better Than Regular Locks And Keys


One of the most common forms of security for the past century has been a lock and key. As technology has progressed, more secure, efficient and convenient methods to protect your assets have been developed. Today, technology allows electronic access control systems to overcome some of the pitfalls of physical keys. Some of the common problems associated with keys include:
-Replacing lost keys
-Re-keying locks to work with existing/new keys
-Waiting sometimes days for a locksmith to arrive
-Making unauthorized physical copies of existing keys
-No door access history
By using a modern access control system such as S2 Security (www.s2sys.com) we can completely eliminate the problems outlined above.
Instead of having a physical key to open a door, a user can be given a specific electronic credential. These credentials come in the form of cards/badges the size of a credit card, fobs that can fit on a key ring, or even your Bluetooth enabled mobile device. Each credential has a unique serial number and is assigned to a specific person. When a door is unlocked, the software will record the serial number and keep a record of who requested access.
In the event that an employee loses their credential, an administrator can quickly disable it and assign a new one to the employee within a minute. This eliminates the need to schedule an appointment with a locksmith, have new keys made, and/or change the lock. In a situation where access is needed but a new card cannot be issued right away, the door can be unlocked remotely by an administrator through S2 software in to allow access.
An employee losing access due to a lost key isn’t as scary as not knowing who may have found it, and now has access to your building until the locksmith shows up. Employees should be trained to notify administrators when they lose a badge so it can be disabled and taken out of the system to prevent unauthorized access.
Another major benefit of an electronic access control systems is the ability to record door access history. If a card is used maliciously to gain access, the date, time, location, and card number are kept on record. The access control system’s timestamp can be used to pull up video of the event on an IP Camera Surveillance System.
An access control system can bring greater security and convenience to your business through the methods we have discussed and more.
Digital Provisions specializes in installing new systems or upgrading legacy Electronic Access Control systems to the latest state of the art IP based systems, all with little or no disruption to your business.
Multi-Floor Elevator Access Control Systems


Controlling access to specific floors that are served by an elevator or bank of elevators is an integral component of a multi-floor access control solution, especially in New York City.
Typical behavior of such a system restricts access to all or most floors other than the lobby by disabling the floor selection buttons inside the elevator cab. When a user presents their credential to the reader in the elevator, the buttons for the floors the user is allowed to access are enabled for a brief period.
Benefits
The benefits of integrating an access control system with building elevators can be significant when paired with good security practices and an access control system such as turnstiles in the lobby. Transient and solicitor traffic in NYC can be nearly eliminated and overall security is increased, with the only real problem left to eliminate being tailgating awareness.
Scheduling
Access to a particular floor or group of floors can be open during specified periods without the need to present a badge if this operation is so desired. This can be used when the reception area is not located in the common lobby and visitors need to see the receptionist before being granted access to another floor.
Additional Security Enhancements
In addition to card readers inside the elevator cab, several other enhancements can be made to an access control system to enhance overall security where elevators and elevator lobbies exist.
High volume optical or barrier turnstiles that require credentials to get into the main elevator lobby can eliminate unauthorized individuals from gaining access to the elevators and other secure areas.
Remaining Security Concerns and Vulnerabilities
Installing an access control or card system in the elevators of a multi-tenant or multi-use building provides added security and control over the movement of people in the building. There, however, are a few social personnel behaviors that require training to identify and curtail to maximize the benefits of such a system. These issues center on basic etiquette that most people have come to follow when on an elevator, but are contradictory to overall security.
The most common behavior that will need to be modified will be the offer to push a floor select button for another elevator passenger who is not in front of the panel themselves. Tenants of the building should be made aware that there is a possibility that they could be taken advantage of to circumvent the security in a situation like this and that any person wishing to get to a particular floor should present their badge and make their own selection.
If a turnstile system isn’t present in the lobby, there is the potential for individuals to simply step on the elevator and ride it until someone requests the floor they want to access, either from inside the cab or from another individual pushing the call button from the floor itself.
In a busy building, this could happen fairly quickly, and the behavior goes unnoticed. Mitigating this possibility can be achieved with the addition of secure lobbies on each floor, where credentials are required to gain access to any area outside of the elevator lobby. Additionally, security guards monitoring video cameras inside the cab would be able to notice a loitering individual and act appropriately.
Digital Provisions specializes in upgrading legacy EAC systems to the latest state of the art IP based systems. We are also your choice for installing new Electronic Access Control systems, all with little or no disruption to your business. Contact us for further information at 631-209-2600.
Stopping Door Propping Using Modern Access Control Systems


Building security is more than just burglar alarm systems and IP video surveillance systems. Modern Access Control systems offer users better control over their building’s overall security. A recurring problem that we are often asked to solve in New York City is the issue of employees propping open building doors. Smoke breaks, impromptu ventilation, deliveries, there are many reasons an employee will stick an object in the doorway to prevent the door from closing. They are probably thinking of just closing the door at the end of their shift but instead, they forget, and so the door remains open all night.
Modern Electronic Access Control systems, such as those manufactured by S2 (www.s2sys.com), have the ability to notify management that a door has been propped, allowing them to take action. Alerts can be configured only to be sent if the door is propped for a specific duration, so deliveries taking up to 10 minutes, for example, will not cause an alarm condition. Even doors that do not have a full electronic lock installation can be set up for this by simply running a wire to the door and adding the proper door sensor which can save money.
Alarm systems have the ability to tell you if a zone is faulted but often users just bypass the zone out of habit and the door remains unsecured. Getting an email from the Access Control system to one or more members of your management team is the most reliable means of making sure all your doors are properly closed.
Additionally, any door set up for door prop alarms can also be configured to send an email every time the door is opened. Further reporting can be added letting you know if the door was opened from the inside or the outside. If for example you have an exterior door that should never be used for entry, a ‘door forced’ event may be configured to alert you if someone came in from the outside.
Building lockdowns can also be initiated from your Access Control system and the system can show you a map of any doors that are not currently closed. Even your HVAC system will run more efficiently when all doors remain closed.
Save money and keep your staff properly protected by ensuring that all doors in your facility are adequately secured.
Digital Provisions specializes in upgrading legacy EAC systems to the latest state of the art IP based systems. We are also your choice for installing new Electronic Access Control systems, all with little or no disruption to your business. Contact us for further information at 631-209-2600.
Eliminating Employee Alarm Codes Through Alarm System And Electronic Access Control


Managing alarm system codes for groups of employees can be a daunting task. With each new dismissal and hire, you must remove the previous employee from the alarm system user list and add the new hire. Often this process involves software or tools that were designed in the 1990’s and are not user-friendly, sometimes even requiring an older PC be kept around just to accomplish the task (raise your hand if you have a Windows 98 computer running somewhere in your building just to keep an old system online).
Few alarm systems offer ease of use as a web-based access control system offers. Such systems, like those from manufacturer S2 (www.s2sys.com), can relieve many of the pains associated with employee administration and security.
Integration of your alarm system and access control systems can substantially eliminate the need for all but one or two key operational personnel to have codes for the alarm system. In many instances, you can completely remove the need for daily opening and closing staff ever to touch or see the alarm keypad. The system greatly simplifies the management of the physical security of the building and improves the employees experience interacting with the building security systems and procedures.
A Single Point of Management
Your electronic access control system contains employee information and is already a point from which you grant and revoke access to different areas of your facility or facilities. Granting and revoking, arming and disarming privileges of the local alarm system can be just as easy as adding or removing a user from an access group or level. Many high-end access control systems offer simple to use end user management features that rival the capabilities of a stand-alone alarm. Features such as time specification (a window of time where access can be granted or denied) and credential activation and expiration dates are not something usually available through alarm management software.
A New Interface
Modern readers such as those from HID allow for enhanced user interfacing and information at each door. These readers provide a multicolor LED lamp allowing for simple color-based security intelligence right where employees are coming from and going. An employee can look at the reader, see if its light is red, and instantly know the building’s alarm system is armed.
In a typical integrated solution, using this reader, how to disarm an integrated alarm system is as follows:
- LED red – Alarm System is ARMED and area is locked
- User presents credential to reader, which is either validated or denied
- Validated credentials result in LED turning blue; signifying alarm has disarmed
- The user presents credential again to gain entry, LED turns green signifying access granted, and the door is unlocked. Once an entry has been completed the LED turns to blue again.
Arming an integrated alarm system involves invoking a procedure known as “double-present.” It is where the user presents the credential to the reader, removes it from the reader and presents it again within 5 seconds. Validated users doing this will result in the LED turning red, signifying the alarm has been armed. Alternatively, a specialized reader may be installed which is only used to arm the alarm system.
Risk of Lost Credential
There is a valid security concern that can be attributed to the integration of an electronic access control and burglar alarm system which uses physical card or key fob type credentials only. This threat can be mitigated by implementing certain HR practices, using specialized hardware, or by combining both. HID Prox cards or HID I-Class type tokens or key fobs can be stolen and then used to gain entry to a building before the user has notified HR. Policies should be put in place that instructs employees not to have anything that identifies the company or building address on the keyring or stored with the card credential.
If the idea of a lost key fob or badge concerns you, enhanced security can be achieved by requiring a PIN code along with a credential presentation to disarm the alarm system. This PIN is still managed in the access control software. Therefore, the benefit of a single point of management for building security is still realized. The PIN will only need to be entered when the system is armed so it will not affect normal access to the door once the system has been disarmed.
Additionally, automatically generated reports may be scheduled to show you arming and disarming activity in the system meaning you no longer need to rely on your central station to provide these to you.
Digital Provisions specializes in upgrading legacy Electronic Access Control systems to the latest state of the art IP based systems, all with little or no disruption to your business. Contact us for further information, or if you have a Windows 98 machine begging to be put to rest.
