Category: Blog
How COVID-19 Made Security Systems Planning Essential Part Business Continuity Planning New York

 One thing the shutdown during the Coronavirus pandemic in NY certainly has done is interrupted many businesses and made Owners question how well they have planned to ensure business continuity in all aspects of their business.
One thing the shutdown during the Coronavirus pandemic in NY certainly has done is interrupted many businesses and made Owners question how well they have planned to ensure business continuity in all aspects of their business.
COVID-19 has exposed vulnerabilities in both processes and systems, including security systems, and the lack thereof when a business moves from onsite work to remote and offsite work. It has also created the need for new standard operating procedures to be developed and managed remotely. And when a business has moved offsite or even temporarily shut down, in many cases, it has left its facility vulnerable to security breaches both physical and digital in nature. Despite the temporary lockdown, every piece of property must be secured.
Therefore, part of any Business Continuity Planning is security planning for your business and risk management. First, let’s understand Business Continuity from a higher level:
What is Business Continuity Planning (BCP)?
A Business Continuity Plan or BCP is the process involved in outlining procedures on how a business will continue to operate during an unprecedented event. Having a prevention and recovery plan ensures a company has the capacity to run its critical business operations during emergency situations. Emergencies can include pandemics, business crises, workplace violence, natural disasters and other events that can disrupt business operations.
Important Factors To Consider When Creating A Security System Business Continuity Plan
- Safety of Employees and Customers. Thermal Temperature Screening is fast becoming the preferred method of screening staff and patrons entering your facility. While not a perfect solution, these systems show everyone that you take this situation seriously and are taking steps to ensure their safety.
- Security of the Company’s Premises. It is said that idle hands are the devil’s workshop. Vandalism has increased during this time and no doubt will continue to be a major concern going forward. A professionally installed burglar alarm system coupled with high definition cameras go a long way in protecting your building, and your peace of mind.
- Company/Team Communications. New technology such as Zoom video conferencing and Microsoft Teams have enabled staff to continue working as one group, even when they are all stationed remotely.
- Alternative Work Locations. Many businesses have relocated staff to satellite offices. When doing so they may find that their Access Control (keyfob system) just isn’t up to the task. A properly designed modern Electronic Access Control (EAC) system will allow you to bring new locations online quickly while managing them all from a single user interface.
- Customized Security Services. Everyone’s security needs are unique. Our team of Security Consultants will help you tailor a customized solution that fits your needs and your budget.
- Security Resource Planning. Using Digital Wellness Planning we can help you apply your current security infrastructure to enforce your new health and safety policies.
- Security Assessment to Prevent and/or Minimize Disruption. We have always offered a free onsite security assessment of your school or business and have now added new guidelines which have been outlined by the CDC and FDA during the pandemic. We will provide you with a report that outlines your current situation and offers valuable information and guidance on how to improve your overall security.
- Damage Assessment and Recovery Team. Should you suffer damage to your premises, we can work closely with your architect to get you headed in the right direction in regard to your security and low voltage needs.
Why Business Continuity Planning Matters
Because continuity means consistency. Consistency impacts more than just Operations and profitability; it impacts market perception and ultimately trust in your brand, an invaluable intangible that then impacts the value of your business.
The Business Continuity Planning Process As It Relates to Security System Planning & Integration
The four stages of a business continuity plan in regard to your security systems are typically:
1) Business Impact Analysis: We will work with your team to gather all of the information needed to complete our security assessment.
2) Recovery Strategies: We will identify weak points in your security infrastructure and offer solutions to offer better redundancy and operation.
3) Plan Development: We will develop a plan that offers solutions to your current security infrastructure concerns. We will also educate you on the latest technology which may help you better handle an emergency situation.
4) Testing and Exercises: Once improvements have been made, we will conduct field exercises to test the new system capabilities and properly train your staff on what to do when things start to happen.
Security System Products That Reinforce Your Business Continuity Plan: A Closer Look
 Looking at business continuity from just a security systems point of view, there is a lot that can be done to help a business maintain superior security levels while decentralizing its operations for example. Business continuity programs should therefore include all of the necessary systems to maintain and improve your business security too. Here are five things Digital Provisions recommends to significantly improve your business continuity program (BCP) as it related to New York Business Security:
Looking at business continuity from just a security systems point of view, there is a lot that can be done to help a business maintain superior security levels while decentralizing its operations for example. Business continuity programs should therefore include all of the necessary systems to maintain and improve your business security too. Here are five things Digital Provisions recommends to significantly improve your business continuity program (BCP) as it related to New York Business Security:
Remote Security System Access – Both your video surveillance system as well as your intrusion (burglary alarm) and EAC systems should be accessible remotely. Additionally, each should be sending you real time updates about certain conditions that you have outlined as requiring your notification. Lastly, a second backup internet service provider (ISP) is an excellent way to provide redundancy into your organization while you are not there.
Intruder Alarm Systems – A properly functioning intrusion alarm system must be monitored by Central Station operators to be truly effective. We sometimes have customers choose to self-monitor and later regret it when they miss that critical call either due to bad reception or being out of pocket. Central Station is always going to respond and they can be instructed to call the authorities if they are unable to reach the designated contact at your organization.
Backup Power Supplies – Every component of your security systems must be connected to some form of backup power supply. A UPS will ensure your system is unaffected by power spikes or short power outages. For further protection a backup generator system is recommended.
Video Surveillance Floorplans – Your video surveillance system must be capable of displaying your cameras on a floorplan of your facility. This will help staff and possibly first responders better deal with emergency situations.
EAC Threat Levels – Your Electronic Access Control system should have the ability to apply predetermined security templates in relation to the security challenge at hand. What is a threat level? Think of it as a way to set specific security measures in motion whenever there may be a problem. By pre-defining your actions, you can instantly place your building into lockdown or take other actions, all automatically.
Additional Reasons Why A Future with A More Decentralized Office Structure Will Impact Digital & Physical Security Planning in the Long Term
 We may never go back to exactly how things were before COVID-19. I think many of us know that to heart. That’s because any challenge, any tough situation, often has a silver lining where new ideas and new solutions are generated. Solutions that can fundamentally change how we operate as businesses. When those solutions improve profits or drive incremental revenue or new profits centers are created, the financial impact alone can be enough to prompt permanent change. One example is curbside pick-up for retailers and food. Is there a reason to not offer this into the future? Coupled with financials is the fact that many of these shifts were already in play around the Globe. For example:
We may never go back to exactly how things were before COVID-19. I think many of us know that to heart. That’s because any challenge, any tough situation, often has a silver lining where new ideas and new solutions are generated. Solutions that can fundamentally change how we operate as businesses. When those solutions improve profits or drive incremental revenue or new profits centers are created, the financial impact alone can be enough to prompt permanent change. One example is curbside pick-up for retailers and food. Is there a reason to not offer this into the future? Coupled with financials is the fact that many of these shifts were already in play around the Globe. For example:
Remote work was already a trend. Data security will be more important than ever. With a trend toward remote work and at-home work already in process well before COVID-19, the current situation has been a catalyst to even more at-home work and potentially permanent restructuring of many business’ infrastructure and workforce. Combine that with an increasingly international and global world and the vast improvements in technology and communication, many questions where in person work is the most optimal system to begin with. Needing to keep your business and information secure in this new environment is critical.
Working with less overhead means leaner and more profitable operations. However, businesses will still keep their buildings for a more “hybrid” approach to scheduling home/at office work. As many companies will learn, to work smarter and “leaner” in terms of personnel and organizational design, the COVID-19 at home workforce may in fact stay at home into the future if it proves to be beneficial for business profits and is acceptable and desired by the work force. However, they will still need to be able to manage security offsite and onsite with equal ease of control, including from mobile devices and 24/7. Remote access control will be increasingly more important, we suspect. Perimeter control will continue to be essential, because it is your first line of defense. All of these systems need to be integrated and also kept up to date, all the time.
Employee scanning will be important on site. Whereas IP cameras were used primarily for security, they will increase function and scan for elevated temperatures and potential health issues. This is part of ensuring a healthy work environment and will continue to be important to future of security. Keeping people out will be balanced with ensuring the health of those you let in; security systems will help this process immensely.
Summary
Has COVID-19 changed the New York business landscape forever? When we look back, will we say it actually has helped us manage our businesses better? COVID-19’s silver lining is that has exposed weakness we can now correct. What does this mean for you the New York business owner? Never before has business continuity planning been so important to keep workers safe and secure, ensure smooth operations, build contingency plans that reduce risk, and make businesses less vulnerable overall to the changes that are inevitably happening in society from COVID-19. Security systems play a large role in ensuring you are reducing risk.
Contact Digital Provisions to Plan A Security Business Continuity Program for Your Business
Plan to put your business in a better more secure position. When you think about BCP going forward, also think about your security continuity. A little planning will go a very long way.
Contact Digital Provisions today at 631-209-2600 for a security consultation.
Additional Resources:
Here is a resource with both a system to self-assess your risk levels but also six steps to create your own business continuity plan: https://www.ilo.org/wcmsp5/groups/public/—ed_dialogue/—act_emp/documents/publication/wcms_740375.pdf.
Lockdown Systems and Visitor Management Systems – What Are The Differences And Benefits?

 Now that the school year is in full swing and budgets are being prepared for next year, the topic of conversation once again is school safety. There are numerous reports about schools implementing new and improved security procedures. Understandably, it is not always easy to make heads or tails of the different technical lingo. For example, you may be hearing a lot about “Visitor Management Systems” or “One Button Lockdown” but really, what are these security tools and what are their differences? More importantly, what are the benefits of instituting them?
Now that the school year is in full swing and budgets are being prepared for next year, the topic of conversation once again is school safety. There are numerous reports about schools implementing new and improved security procedures. Understandably, it is not always easy to make heads or tails of the different technical lingo. For example, you may be hearing a lot about “Visitor Management Systems” or “One Button Lockdown” but really, what are these security tools and what are their differences? More importantly, what are the benefits of instituting them?
A Visitor Management System (VMS) is a complete and systematic approach to managing all individuals stepping foot on a school’s campus. It is a simple tool that schools or corporations can use to completely vet an individual before admitting them inside a facility.
Upon entering a school, or before if you have mantraps, the visitor will be met by a security guard who will ask for proper identification, driver’s license or state ID card. Their identification will be run through the VMS system which will screen that person against the National Sexual Predator database. It will also bring up any critical information that is security centric, such as a restraining orders or custodial flags that might be on file.
Additionally, a log of notes can be kept by school security from prior visits, such as “visitor became verbally abusive last visit” etc. Once the visitor is granted security clearance, they are given a temporary identification badge that is turned in, or expires (changes color), after their visit is complete. With this badge, they are visibly identifiable during their visit. Likewise, anyone who does not have this badge, can be immediately challenged and ushered back to security.
One Button Lockdown Systems give you the ability to lock down an entire school, or an entire district at the push of a button. No one wants to imagine an emergency happening at their local school – but if something did occur, you can be prepared. One Button Lockdown allows designated school officials to push a single button to initiate a chain of events to secure the building. During this lockdown, interior and exterior doors shut and lock, exterior strobes flash to warn anyone entering the building to leave, interior displays on phones and computers flash that a lockdown is underway, a prerecorded announcement by the superintendent or principle sounds on the P.A. system, and if desired alert messages are sent updating parents and staff in real time.
Most importantly, the police emergency management call center is alerted of the lockdown situation with crucial information, location and cause. This emergency button can either be wall mounted, on a computer, or on your cell phone and you can choose to lockdown just your school, or the district as a whole.
In comparing these two security measures, it is evident that the whole is greater than the sum of its parts. Visitor Management Systems control the flow of visitors into the building to prevent any emergency situation from occurring while One Button Lockdown security systems control the entire environment of the school if an emergency actually occurs. Both security measures, the goal is to identify any potential threats to staff and students, and thwart any sort of emergency should one take place.
Digital Provisions designs customized security solutions that match the safety needs of schools and corporations on Long Island, NY. Contact us today to schedule your FREE Site Security Design.
School Safety: Having The Right Tools Means Better Overall Security


Having worked in a school setting, I can honestly say that the security of students and staff is on your mind all day long. From the moment you step foot in school in the morning, to the minute that bell rings at the end of the day, keeping your students and staff safe is your top priority.
Part of the struggle in keeping schools secure is quickly and effectively reacting to a situation with as much accurate information as you can possibly obtain. A stranger at the door, a car approaching the gate, a loud sound in a remote area of the building – these are all scenarios that happen on a regular basis and many times are perfectly harmless. However, to truly be prepared in any given situation, you must first be ready and equipped with the proper tools for the job.
Violent or threatening incidents in a school environment are happening across the country at an alarming rate and school security has become an increasingly hot topic of conversation. The good news is that many schools are responding to this by implementing or adjusting their safety procedures in hopes to diffuse a volatile situation.
The bottom line is that school safety is about being vigilant. To successfully monitor your surroundings, it is paramount to upgrade your school’s security surveillance system. Being proactive and collecting as much information prior to an individual stepping foot inside your school building is the best and safest way to proceed. In order to achieve this, it is crucial to install security cameras with high resolution imaging. Installing access control systems in different areas can also help oversee the flow of people in and out of the school building.
The benefit of having an effective school security system is the ability to control your environment from a safe vantage point. From your computer screen, you can view real time images, zoom in on faces and license plate numbers as well as any other minute detail that could illicit action and diffuse a situation. Having each staff member equipped with a key to enter the building is also a proven method to keep a building secure.
In having the proper security equipment, you are actively choosing to do all that you possibly can to assess a situation to achieve a safer result.
Digital Provisions believes in providing smart and proactive tools to maintain a level of safety and security for all students, teachers, fellow community members and all who spend their days in our schools. We specialize in designing and installing audio and visual surveillance specifically geared for schools on Long Island and New York City.
Contact us to learn more about the tools and technology we offer to keep your school safe and secure. Call 631-209-2600 to schedule a FREE site security design.
Article Written By Lindsay Butler
Prevent Crimes From Happening Outside Of Your Commercial Building


Commercial burglar alarm systems may be boring but as everyone knows, they protect the inside of your business against someone breaking in to steal your valuables. It’s a simple concept that has been around for over 100 years. But what if there was something new, a new type of system that did more than protect just the inside?
Digital Provisions designs and installs burglar alarm systems that do more than keep your inside valuables safe, our systems can now keep everything safe on the outside of your commercial building too, out in the open, no fences required. Recently one of our clients had their system go into action and prevent the theft of some very expensive automotive parts.
Recently, on an early weekday morning, two perpetrators set out on a plan to steal rims and tires from a local Toyota dealership. The suspects parked in a nearby medical building parking lot and stealthily maneuvered all of their tools to the gas station adjacent to the dealership. From there, they moved with their tools over to a car on the front line of the dealership’s lot. Brazenly they began jacking up the vehicle, only pausing briefly when the occasional car drove by. What they didn’t know was that they had tripped a silent alarm the moment they stepped onto the lot. As they were busy undoing lug nuts, our central station operators were logging into the dealership’s security camera system to see what had tripped the alarm.
That alarm verification procedure is the key to any successful exterior protecting burglar alarm system. Without it there would be too many false alarms and the police would stop responding, not to mention fine you for all of the false. With a live operator looking at the cameras in real time, they can assess the entire property in minutes, something that an onsite guard would not be able to do for instance so easily. When the threat is verified, they can contact the police and tell them exactly where the incident is happening on the lot and what they should expect when the police arrive.
Back at the dealership, when the central station operator witnessed that a crime was taking place, he immediately challenged the suspects over the security system’s external loudspeakers. “Attention – you are not permitted to be on the lot at this time!” bellowed out of the system, stopping the intruders dead in their tracks. Startled and scared, they instantly fled the scene, leaving behind their tools and more importantly, the dealership’s very expensive rims and tires.
There is no guarantee they would have stopped there either. Very often thieves will target a particular location for more than just one item. This can leave business owners with multiple cars up on blocks or multiple trucks broken into. There is no limit once they know they can safely stay on your property without anyone knowing about it.
Police arrived on the scene, and the suspect’s tools were taken into evidence. The customer’s inventory remained protected, and the crime was prevented with no loss of property or damage to the vehicle.
Digital Provisions specializes in installing commercial security systems, inside or out, all with little or no disruption to your business. Contact us for a no-obligation site security design which will give you the information you need to properly secure your property and your peace of mind.
Score 1 for the good guys. Check out the video on our Facebook page – https://www.facebook.com/digitalprovisions
Manage Important Employee Information Using Access Control Systems

Modern access control systems can help you better manage employee information while still performing its primary function, which is to secure your facility properly. Your Electronic Access Control (EAC) system can be used to store important employee information such as contact info and vehicle info both of which are relevant to using your EAC system. Advanced systems like those from S2 (www.s2sys.com) can also house other data for each employee using custom fields.
Many organizations will define custom fields to hold data such as emergency contact info, department info, vacation days or anything else that you need to keep stored. Custom templates may also be configured which allow you to make entering new employees easier while maintaining uniformity amongst different records.
EAC card credentials can also store information and be used for employee identification while on the job. You can store each employee’s picture with their person record and then print this directly onto their credential. This essentially gives you an ID badge and key to unlock doors all in one card.
Employee credentials may also be used in conjunction with time limits. Credentials may be set to expire after a certain timeframe, very useful for temporary employees and other unique situations. You may also decide to set a policy in which credentials automatically expire after certain period passes in which they have not been used. This helps prevent lost credentials or fired employees from being granted access into your building. And don’t worry, you can be alerted by email before a credential is going to be deactivated, allowing you to take extended leave situations into account and postpone the deactivation.
Person Trace is a very useful tool for managers to use in conjunction with employee issued credentials. Your system should allow you to flag a particular user’s person record. Once flagged, the system will automatically trace all activity and automatically create an event every time that credential is used. You will also find it useful to run user activity reports which will allow you to filter on and focus on any event type you wish like access denied events for example.
Digital Provisions is specialized in installing and upgrading any type of Electronic Access Control Systems to a more advanced IP-based system. Contact us at (631) 209-2600 for a no obligation site security design. Our access control specialists will give you the information you need to properly secure your facility.
Protecting Your Car Dealership Against Invalid Claims: A Video Surveillance System Is Your Ally

It’s becoming a problem in our society with people being able to sue anyone for anything these days, more often than not most claims are false. People are always trying to get over on somebody else’s dime, but this doesn’t have to be you.
Through the use of advanced video surveillance, and audio surveillance, you can protect yourself and your company from liability – if you have a properly designed system. Recently one of our customers who owns a large new car dealership has been using his system for this exact purpose, for protection against invalid claims.
Here are two examples:
A customer claimed to the dealership that his vehicle was damaged when in for service, large dent on the rear quarter panel. The dealership’s owner reviewed the footage of the car entering the shop and the large dent was already on the vehicle, obviously not done by the dealership. He was able to send an image to the customer of the condition of the car prior to entering the service shop because he had a properly designed system that was viewing vehicles entering and exiting the service shop.
Same dealership but different scenario, customer claims sales person took over an hour to come and greet/help her. The customer wrote a bad review online referencing horrible customer service at this dealership. The dealership contacted the customer who made the claim and asked for the time and date of the occurrence. When going back to the video it was discovered that this customer was greeted within 60 seconds upon entering. The bad review that was posted online was retracted when the customer was shown the proof.
These two examples are just the tip of the iceberg when it comes to verifying a claim that someone makes against the actual truth. Having a video surveillance system saved this dealership a lot of headaches, possible bad reviews but most importantly money. Security cameras are a necessary tool in business, the key is to have a system that is tailored to your specific needs in order to be effective.
Contact us to find out how this proven new technology can protect your assets and your property. Even better, call and ask for a free car dealership security systems design to see how the system should be laid out and what investment will be required.
Does Your Access Control System Tell You All About The Day’s Activities?
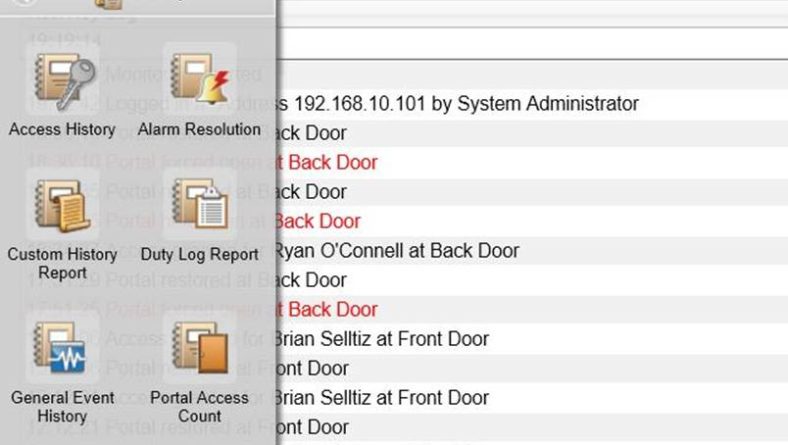
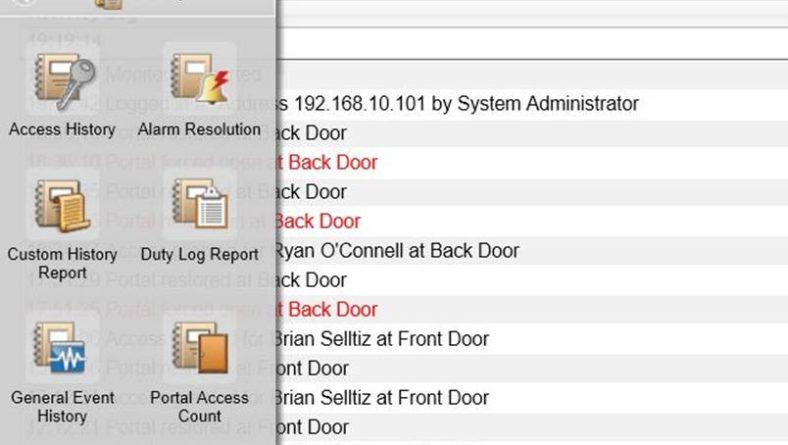
Does your EAC system speak to you? Probably not, but that doesn’t mean it shouldn’t communicate important information to you on a regular basis. Access control reports are a powerful yet often underutilized function of a modern access control system. Systems such as those manufactured by S2 www.s2sys.com offer users a powerful interface which allows managers to get the information they need about their building in real time. Additionally, reports can be automated to arrive in your inbox at a specified time or day.
Some of the more common reports are:
Access History Reporting
Parameters: Person; Event Type; Date Range; Door ID
Best Use Examples:
-Where is ‘Harold’ always disappearing to? Run a report to see when and where ‘Harold’ has been during the last month.
-Think an employee is testing out to see if the door is locked to that secure storage? Run a report to see every time someone tried to get into an area where they did not have the proper access to do so.
-Had an incident at the plant needed more info? Run a report to see everyone who was in the office on the day in question.
-Weekend hijinks? Automate a report to email you every Monday morning to show who was in the building over the weekend.
Compliance Reporting
Parameters: Door ID
Best Use Examples:
-Do you have schedule II drugs or other items that require only certain people access that storage area? Run this report on demand to confirm who has access to critical areas. Even better, automate this function, so it is delivered to your inbox at the beginning of the month like clockwork.
Credential Audit Reporting
Parameters: Time Span; Credential Status
Best Use Examples:
-When an employee is terminated their credential should be disabled, but we all know that sometimes things get missed. Run this report to see who has not used their badge in the last 30 days and then disable it.
-Vendors are notorious for never returning badges (not us of course). Run this report and quickly identify vendors who no longer require access to your building and disable their badges.
Utilization Reporting
Parameters: Date Span; Door ID; Person
Best Use Examples:
-Most often we see this report used to deliver relevant statistics on Turnstile utilization. Turnstiles are now standard security equipment in larger buildings throughout New York City / NYC, use this report to get true numbers of people passing through per week, month, year, etc.
Digital Provisions specializes in installing and upgrading Electronic Access Control Systems to the latest state of the art IP based systems, all with little or no disruption to your business. Contact us for a no obligation site security design which will give you the information you need to secure your facility properly.
Is Video Surveillance Enough To Truly Protect Auto Dealerships?


Many business owners invest heavily in video coverage, but often end up only recording crimes against them and not apprehending the criminals or preventing the crimes from happening. While traditional video and audio recording systems can provide automotive dealerships with a host of valuable information (see “Video Surveillance – Beyond Security”) they do little to deter criminals from committing crimes. By itself, an auto dealership video surveillance system does nothing to protect a lot from attack, serving merely to document the incident and perhaps yield a few clues.
In a recent example, a Texas Chevrolet dealer endured an extensive heist that left 48 cars without wheels and tires, at a cost of approximately $250,000 in damages. The event was captured by the dealership’s extensive array of security cameras, however despite being on the property for approximately 4 hours the perpetrators went undetected during their caper. A small amount of valuable information was collected from the video of the incident but the crime wasn’t discovered until the next day. Having not captured anything uniquely identifiable the video evidence is useful only in establishing a timeline for the crime and provided very few additional clues.
Remote Guarding with Interactive Audio Challenge
With the advancement of a host of different technologies, remote guarding has become a viable solution for protecting car dealerships and other outdoor lots with vehicles or equipment under threat of burglary or vandalism.
Remote guarding leverages the power of high definition video, audio, advanced motion and perimeter breach detection systems with the internet and remote security agents to form a substantial level of protection for an outdoor space. Considering the ability to have 360 degree coverage all the time it can easily be argued to be more effective than a vehicle based roaming guard service.
Live audio interaction with the property changes the game against a criminal. Knowing they have been detected and that police are on the way will generally put an end to the crime. The shock value alone of a loud voice piercing the night while they are committing a burglary is incredible.
Properly designed systems can have a live agent challenging a suspect via loudspeaker in around 3 minutes of them breaching the perimeter. This is a powerful tool that works almost as soon as the threat is established, reducing and even eliminating damages or loss of property.
System Design and Installation
Effective protection of a car dealership or similar lot begins with understanding the unique vulnerabilities of the particular location. To properly recognize the threats a lot is subject to, a detailed forensic threat analysis is required. During this process our team would identify weaknesses in the physical perimeter, potential or active routes of attack, site lighting conditions and other environmental factors that impact security of the perimeter and pathways throughout the interior. We examine and inventory the current security infrastructure (if it exists) to determine which if any components can be incorporated as part of our design.
With the threats understood a formidable defense can be designed. Each system is engineered from a core base of components, but no two systems are exactly the same. A well designed system will have solid perimeter protection and good spot motion coverage throughout the interior of the lot. Generally the installation will require some coordination with the IT managers as secure connections to the internet will be required.
After the installation is complete the system is tuned to peak performance and minimal false levels. Delivery and cleaning personnel patterns and behaviors are learned and any effects of vegetation are dealt with by either trimming or sensor relocation.
Installed systems are reviewed by our team on a daily basis to establish any false alarm patterns that develop and to observe the general health of the system.
Digital Provisions has been installing video verified intrusion systems since 2011 and knows what it takes to get it done right. Contact us to find out how this proven new technology can protect your assets and your property.
Original article about the burglary incident at a Texas Chevy dealership can be found here:
http://autoweek.com/article/car-news/180-wheels-stolen-texas-chevy-dealership
Back Up Your Access Control System Before It’s Too Late!


In the wake of any disaster, the race is on to restore things to normal. If your place of business is damaged by flood water, fire, electrical surge, or other means, chances are your electronic equipment could be damaged and in need of replacement. If this happens to you, does your access control system provide built in offsite backup? This feature is included in S2 Security access control systems and it can make redeploying your security measures a task that can take minutes instead of days.
In the S2 Security box’s web interface, you will find a feature called “FTP Backup”. This feature allows the user to create a full backup of the access control database and save it offsite at a secure location automatically. Users can always manually download a copy of the database, which is recommended prior to making any major changes to the system.
Each employee will have their own access control cards, access schedules, and other security related data. Having an FTP backup from S2 Security can save countless hours that would otherwise be spent tracking down and collecting individual employees’ access cards, rebuilding the access control database, reprogramming locks and door components, and resetting schedules manually.
The FTP backup method, on the other hand, is a completely different experience. After diagnosing the point of failure and replacing the damaged equipment, the restoration process can be completed in minutes once the off-site backup file is uploaded to the panel. As with any backup method, it is recommended that the data is periodically checked to ensure that the system is working properly and the system restores properly. Simple, automatic and invaluable if needed, be sure to include your access control system in your contingency planning backup procedures.
Digital Provisions specializes in installing new systems or upgrading legacy Electronic Access Control systems to the latest state of the art IP based systems, all with little or no disruption to your business.
Why Electronic Access Control Systems Are Better Than Regular Locks And Keys


One of the most common forms of security for the past century has been a lock and key. As technology has progressed, more secure, efficient and convenient methods to protect your assets have been developed. Today, technology allows electronic access control systems to overcome some of the pitfalls of physical keys. Some of the common problems associated with keys include:
-Replacing lost keys
-Re-keying locks to work with existing/new keys
-Waiting sometimes days for a locksmith to arrive
-Making unauthorized physical copies of existing keys
-No door access history
By using a modern access control system such as S2 Security (www.s2sys.com) we can completely eliminate the problems outlined above.
Instead of having a physical key to open a door, a user can be given a specific electronic credential. These credentials come in the form of cards/badges the size of a credit card, fobs that can fit on a key ring, or even your Bluetooth enabled mobile device. Each credential has a unique serial number and is assigned to a specific person. When a door is unlocked, the software will record the serial number and keep a record of who requested access.
In the event that an employee loses their credential, an administrator can quickly disable it and assign a new one to the employee within a minute. This eliminates the need to schedule an appointment with a locksmith, have new keys made, and/or change the lock. In a situation where access is needed but a new card cannot be issued right away, the door can be unlocked remotely by an administrator through S2 software in to allow access.
An employee losing access due to a lost key isn’t as scary as not knowing who may have found it, and now has access to your building until the locksmith shows up. Employees should be trained to notify administrators when they lose a badge so it can be disabled and taken out of the system to prevent unauthorized access.
Another major benefit of an electronic access control systems is the ability to record door access history. If a card is used maliciously to gain access, the date, time, location, and card number are kept on record. The access control system’s timestamp can be used to pull up video of the event on an IP Camera Surveillance System.
An access control system can bring greater security and convenience to your business through the methods we have discussed and more.
Digital Provisions specializes in installing new systems or upgrading legacy Electronic Access Control systems to the latest state of the art IP based systems, all with little or no disruption to your business.
